Last Updated on 4 months ago by Sachin G
Encrypting sensitive information in configuration files has become a standard best practice, especially in environments managed using Ansible. This article explores how to encrypt or decrypt a string through Ansible Vault—a powerful feature that helps protect secrets and sensitive content across playbooks, inventories, and other structured data files.
We can encrypt and decrypt variables in inventory and playbook variable files, as well as passwords passed as a command-line argument or defined in Ansible roles.
What Is Ansible Vault?
Ansible Vault is a command-line tool that allows users to keep sensitive data, like API keys, email addresses, and private keys, safe within plain text files. By encrypting values or entire files, Vault helps prevent exposure in source control or real-time conversations.
When to Use Vault: Practical Use Cases
Vault is ideal when managing sensitive data such as:
- Passwords for remote servers
- API keys for cloud services
- Encrypted variables within playbooks
- The contents of an encrypted file stored in a version control system
One common scenario is storing secrets in variable files, also known as vars_files or YAML files, rather than hardcoding them.
Encrypting a String with Ansible Vault
Encrypting a string through Ansible Vault is a simple process but we have two scenarios: You already have a variable file or a string file that you want to encrypt or You have to create from starting and insert a variable and encrypt it. First, we will look at creating variable files from starting.
1. Encrypted through Create a Vault File
ansible-vault create filename command will create a new encrypted file, when we run this command then it prompts us to set the password and it opens like in the vi editor.
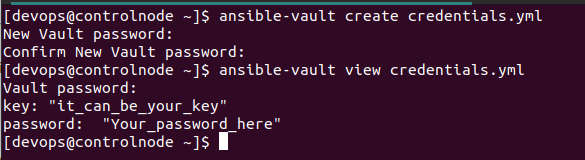
[devops@controlnode ~]$ ansible-vault create credentials.yml
New Vault password: complex_password
Confirm New Vault password: complex_password
In the editor, insert your variable or sensitive information into the file, and save the changes to the Vault file. Below is a screenshot showing an example of creating an encrypted file using Ansible Vault. By using the ansible-vault view command, you can see the encrypted variable. Don’t forget to provide the encryption password when prompted.
2. Encrypting Whole Files or Variable Groups
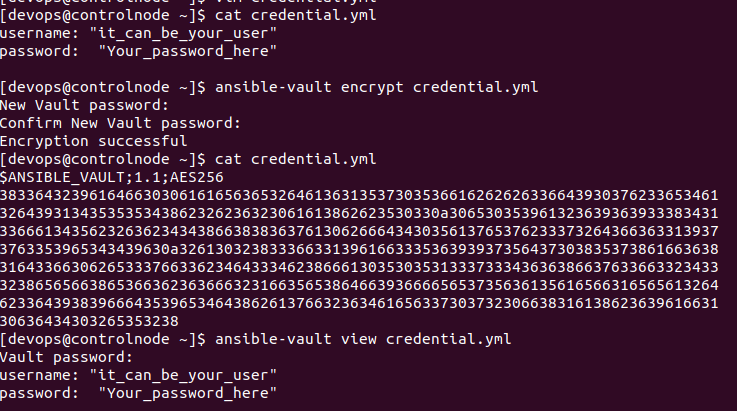
For encrypting an entire file like a credentials YAML, the ansible-vault encrypt The command is used. Generally, we already have a variable file or an existing file that we want to encrypt to protect sensitive information. The command below can be used to encrypt the file by providing its name as an argument. Don’t forget to enter the encryption password when prompted for the first time and confirmation.
[devops@controlnode ~]$ ansible-vault encrypt credential.yml
New Vault password:
Confirm New Vault password:This ensures all sensitive data in the file remains protected, even if the system or user is compromised.
Avoid storing the original plaintext file alongside the vault-encrypted file, especially in code repositories or shared locations.
Decrypting Encrypted Content
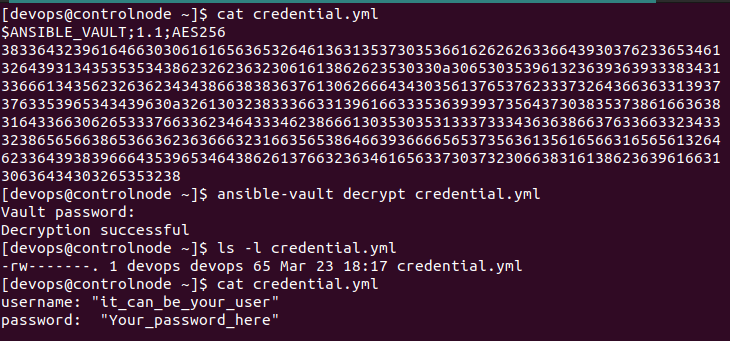
To retrieve the original value of encrypted data, use the decrypt command: Here, we will learn how to use Ansible Vault to decrypt the string of an existing encrypted file using the permanently ansible-vault decrypt filename command. Providing the encrypted filename without an additional filename will decrypt the same file with the same name. Please refer to the screenshot below.
[devops@controlnode ~]$ ansible-vault decrypt credential.yml
Vault password:
Decryption successful
This converts the encrypted content back to a decrypted file, which must be protected during use and deleted afterward to minimize risk.
if you need to only string encrypt from the command line outside of the playbook, you can use the Ansible Vault String command. Below is the syntax to encrypt.
ansible-vault encrypt_string <string_to_encrypt> --name <variable_name>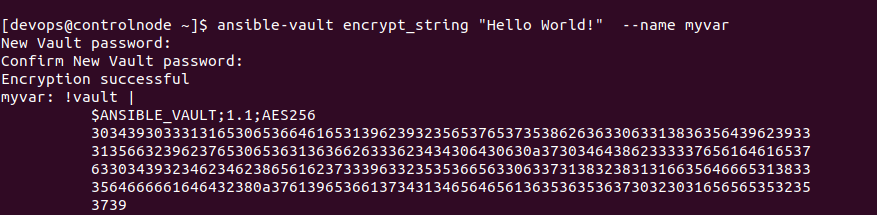
At the end to provide the vault password to the encrypted playbook or encrypted playbook used in the playbook, it will need a vault password, use the –vault-id option. For example to provide the vault password in the command line, use –vault-id @prompt as in the below example.com:
[devops@controlnode ~]$ ansible-playbook --vault-id @prompt playbook.yml
Vault password (default ): your vault password
Debugging Encrypted Values
You can inspect the encrypted value using the debug module:
- name: Show Encrypted Variable
debug:
var: api_keyUse the ansible localhost -m debug command for real-time validation during development.
Additionally, you can follow the Ansible installation on Ubuntu here.

I’m Sachin Gupta — a freelance IT support specialist and founder of techtransit.org. I’m certified in Linux, Ansible, OpenShift (Red Hat), cPanel, and ITIL, with over 15 years of hands-on experience. I create beginner-friendly Linux tutorials, help with Ansible automation, and offer IT support on platforms like Upwork, Freelancer, and PeoplePerHour. Follow Tech Transit for practical tips, hosting guides, and real-world Linux expertise!
