Last Updated on 7 months by Sachin G
Do you want to disable or enable ( enforcing ) SELinux mode on host machines through the ansible-playbook? Here I am writing a playbook to change the mode of the SELinux type. SELinux is an important security feature of Linux. There is three value in SELinux, which is Enforcing, Permissive, and Disabled. The main configuration file of SELinux security is /etc/selinux/config
Enforcing: This shows the security policy is enforced.
Permissive: This value shows the security policy only shows warning instead of enforced.
Disabled: It means the policy is not loaded in the kernel or disabled in the condition.
Selinux is a kernel-based security module, So when you will make a change from Disabled to Enforcing or Enforcing to Disabled, you should always reboot your machine because the system reads the configuration file at boot time.
- The playbook is tested on CentOS Stream 9 Linux Structure. All the identical machines with CentOS 9 machines.
- Before executing this on the production environment you should check on your testing env.
- You should dry run or test run before executing through ansible-playbook -C PlaybookName.yml
- A version of Ansible which I used is ansible [core 2.14.2] or ansible-navigator 2.2.0 Platform.
First Discuss playbook tasks steps :
Task1:Disable or Enforcing Playbook Task
First, we write a playbook snippet to disable to enable the policy. The module we can use is SELinux. This module can configure mode and policy.
Enable SELinux
Below task code will set your configuration file to enforcing mode and policy will set to targeted.
- name: Enforcing SELinux
ansible.posix.selinux:
state: enforcing
policy: targetedDisabled SELinux
In disabling the policy argument is not needed. So the state will be disabled.
- name: Disabling SELinux state
ansible.posix.selinux:
state: disabledTask 2: Reboot the managed host machine
Here I am ensuring in my playbook the configuration files are changing and printing the output in the playbook at run time. After printing the output the machine will reboot.
Ansible Playbook for disabling SELinux with a reboot
Below is my playbook for this task, before executing you should always test on your environment or dry run. Through this playbook, if the system is already in the desired state or disabled then after executing this playbook the managed host machine will not be rebooted. This playbook only reboots when changes occur in the configuration file.
---
- name: Ansible Playbook for disabling SELinux and Reboot .
hosts: srv1.example.com
handlers:
- name: reboot server
command: systemctl reboot
tasks:
- name: Disabling SELinux
ansible.posix.selinux:
state: disabled
register: selinuxdisabled
- name: Print the changes in Configurtion file
ansible.builtin.command: grep SELINUX /etc/sysconfig/selinux
register: sevalue
- ansible.builtin.debug:
var: sevalue.stdout_lines
- name: Wait for 5 Second and Reboot
shell: "sleep 5 && reboot"
async: 1
poll: 0
when: selinuxdisabled is changed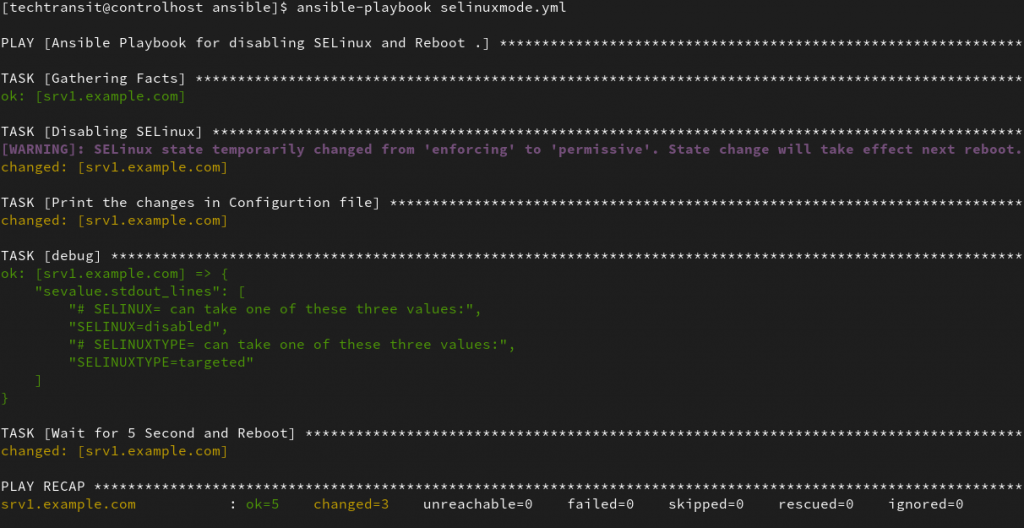
Ansible Playbook for Enforcing SELinux with a reboot
---
- name: Ansible Playbook for enabling SELinux and Reboot .
hosts: srv1.example.com
handlers:
- name: reboot server
command: systemctl reboot
tasks:
- name: Enabling SELinux
ansible.posix.selinux:
state: enforcing
policy: targeted
register: selinuxdisabled
- name: Print the changes in Configurtion file
ansible.builtin.command: grep SELINUX /etc/sysconfig/selinux
register: sevalue
- ansible.builtin.debug:
var: sevalue.stdout_lines
- name: Wait for 5 Second and Reboot
ansible.builtin.shell: "sleep 5 && reboot"
async: 1
poll: 0
when: selinuxdisabled is changed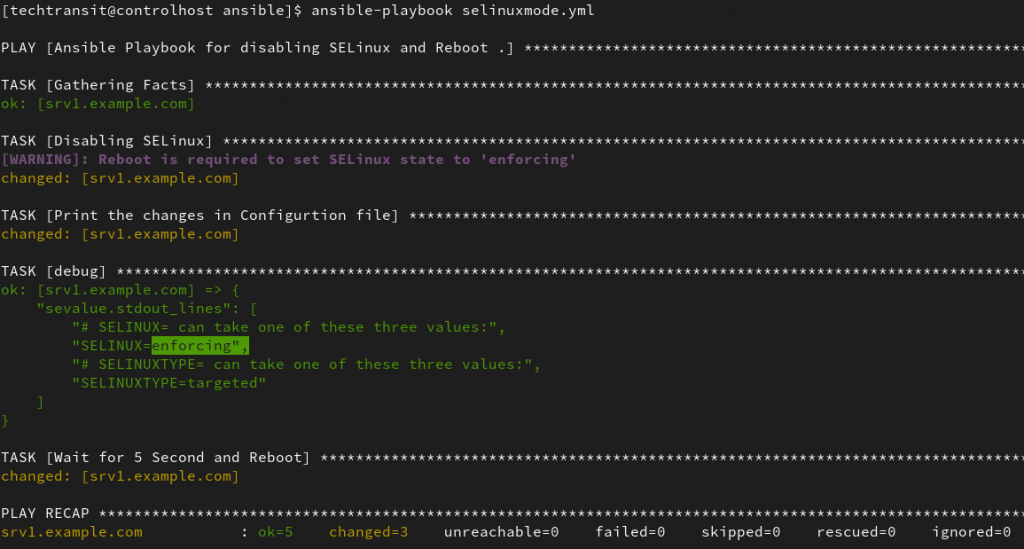

I am a professional freelance contributor and the founder of Tech Transit. I hold certifications in Linux, Ansible, and OpenShift from Red Hat, as well as CPanel and ITIL certifications. With a passion for education, culture, and community, I love writing and sharing knowledge. Since 2009, I’ve been actively using, setting up, supporting, and maintaining Linux systems. Linux truly rocks!

